Acumatica Security: Top 10 Reasons Acumatica Stands Alone
Security has become more of a concern as more data is stored electronically, and hackers come up with new ways to acquire information. How you...

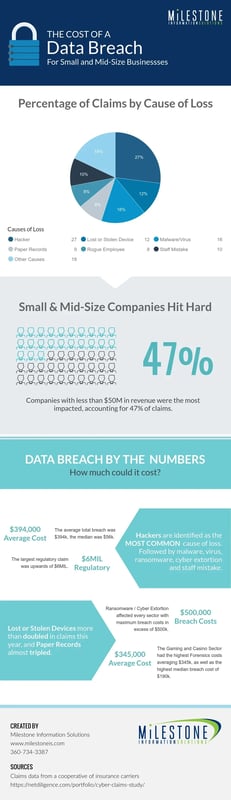
Data security is an constant concern in the small and mid-size business sector, but there's still a perception that only the big companies are a target... they aren't looking for companies like ours. Unfortunately for us all, that's not the case. Despite the large breaches being the news makers, 47% of cyber attacks are focused on small and mid-size businesses, and 50% of small and mid-size organizations reported suffering at least one cyber attack in the last 12 months.
Learn more about what happens, and how with our infographic below - see the complete infographic at the bottom of the article on Acumatica Security Capabilities.
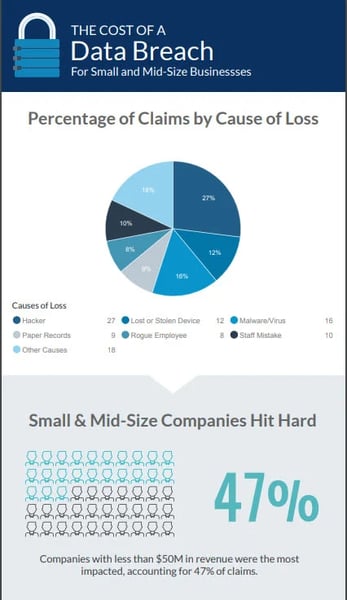
Those are some depressing numbers. Fortunately there are plenty of resources to protect your business. One of your top priorities is definitely protecting your financial information, employee records, customer information and sensitive business data.
ERP software like Acumatica ERP, was built for security, with extensive options to meet your companies security needs. See some of Acumatica's security capabilities.
Unlike many web-based applications, with Acumatica you are in complete control of where your data is stored and processed, and you control who can access and use your system.
Acumatica can be installed at your location or at a Hosting or Cloud Services provider. Hosting providers offer 24x7 staff in physically secure data centers that exceed what most businesses can provide internally - and often at lower cost. For some organizations however, data and processing must be performed internally at locations mandated by governmental or corporate policy. With Acumatica the choice is yours.
With Acumatica all business processes happen on the server side (whether in the cloud, or on premise), and not on the user's computer or in a web browser. This makes it more difficult for an unauthorized user (hacker) to understand, and gain access to your system.
All data, be it customer, vendor, transactional or informational is all stored on your AWS Cloud or on-premise server. As users complete forms only the small bits of data they actually see are transferred through the browser - and even then, only for an instant. Once forms completed and submitted, no data remains in the browser, and no data is ever stored on the user's computer.
To transfer information between Acumatica and the user's browser, Acumatica uses 'https', the same encryption technology used by banks to ensure no one can 'listen in' on your data.
For especially sensitive information, Acumatica encrypts certain fields such as credit card numbers, social security numbers, names and salary information within the database. This protects you in the event a backup copy of your information is lost or stolen. You can also choose to designate any fields you wish to be encrypted.
Row-level security is crucial for businesses with multiple locations or even autonomous departments/teams. Acumatica uses row-level security to restrict a user’s ability to create and access data based on their region or branch location. Data such as financial information and accounts, customers, vendors, budgets, and inventory.
Security policies can be assigned by user or by role. Assigning security settings by role, reduces the chance for error. An unlimited number of roles can be created, so there is no limit to the types of security rights you can grant.
User menus display only the applications, pages, and reports each individual user is authorized to access. Forms, reports, and inquiries will not contain data not authorized for a user. This reduces accidental access to sensitive information and makes Acumatica easier to learn and use from the start.
User logins can be limited to specific IP addresses. You can define how long a user password must be, and how often they must be changed. You define when a user’s browser session times out due to inactivity. One Time Passwords (OTP) systems can also be used to issue new passwords every few minutes, and link to the users cellular phone or a keychain device.
Each transmission between the browser and the application server is re-validated from an encrypted key.
Acumatica maintains a timestamped log of user activities in the system. Some of the events (or activities) tracked are: login and logout, session expiry, login failure, screens accessed, send email success, send email error, and record creator. You can setup notifications for certain events down to field level changes. This information is crucial not just in identifying a data breach, but also where audit trails are a required part of doing business.

Security has become more of a concern as more data is stored electronically, and hackers come up with new ways to acquire information. How you...

The rise of cloud technology has not only transformed business operations but also revolutionized the pricing model for ERP systems. An increasing...
1 min read
The best in ERP technology is moving to the cloud, and Acumatica ERP software is at the forefront. Acumatica was built in the cloud, not adapted for...